Private-Public Key Pair - Asymmetric
Recipient creates a pair of Private-Public keys (using name, expiry, passphrase and algorithm)
Recipient shared the Public key with third parties
Senders user the Public key to encrypt data
Only the Recipient can decrypt data with the Private key
If the Private key is compromised, the Recipient needs to recreate a pair of keys
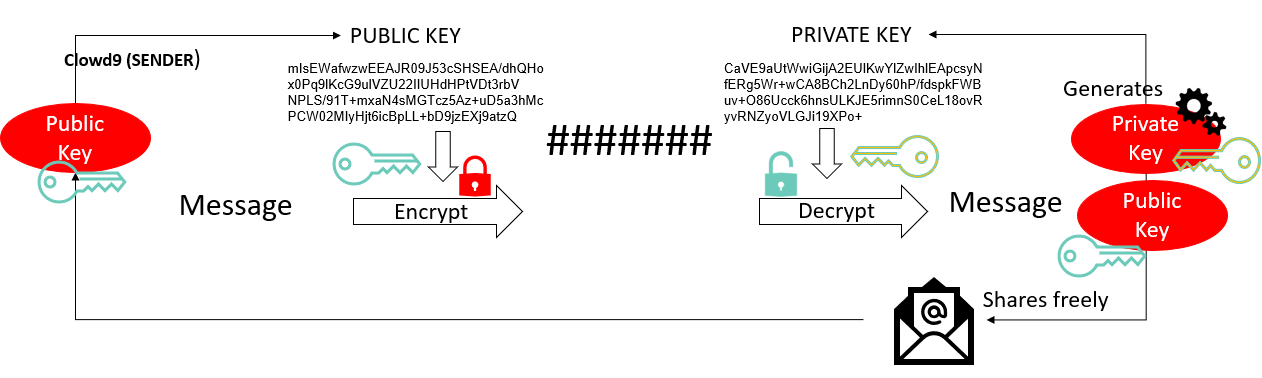
Only the owner of the private key can decrypt it
Public key can be shared non-securely
Private key needs to be securely stored
All entities having the public key can decrypt what is encrypted with the Private key
Private-Public keys are bigger in size than shared keys
Algorithm is more complex and slow than shared keys
How to exchange and use asymmetric keys?
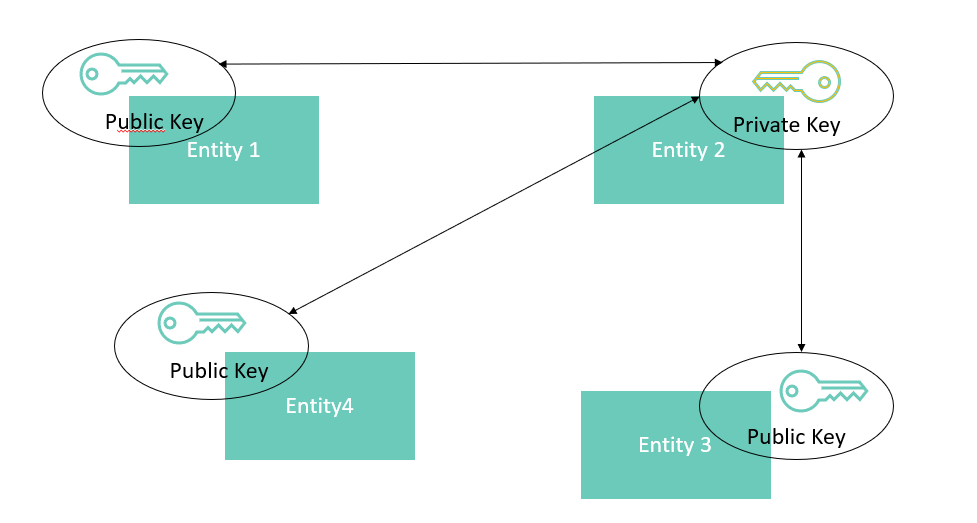
Only Public keys are exchanged
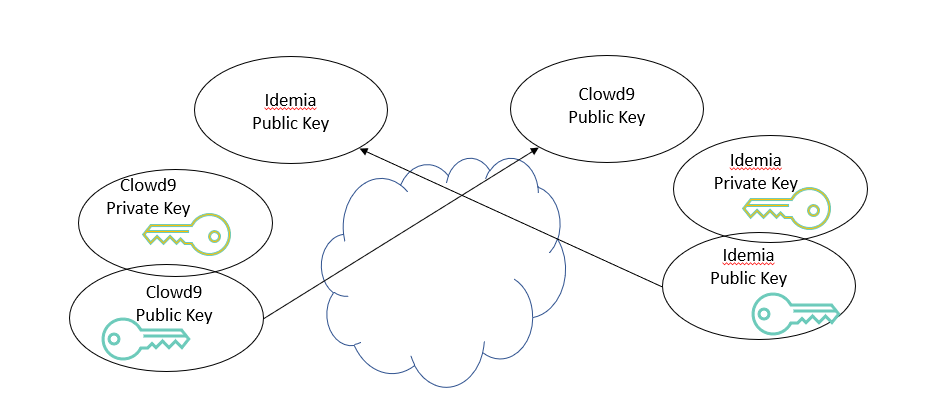
Step 1. Each entity send its public key to the other
- Public key can be sent by email
- Private key needs to be kept secret
Step 2a. Sender uses Receiver’s public key to encrypt it
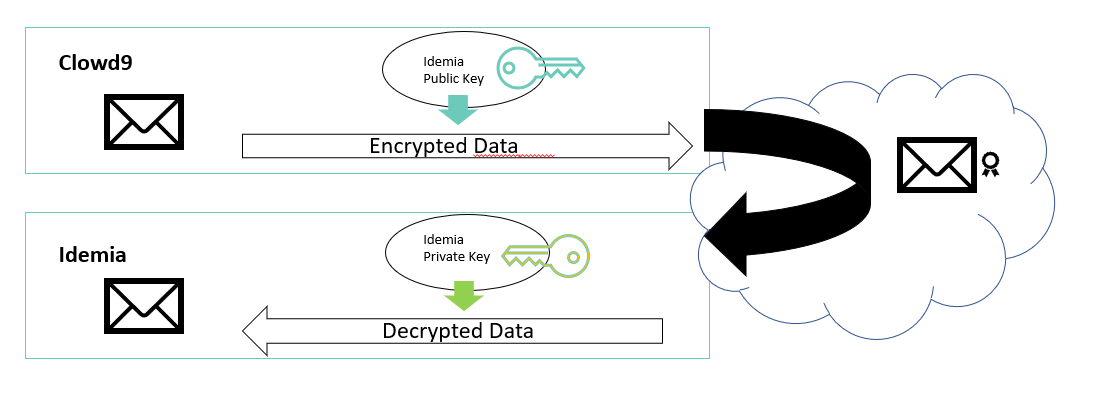
Step 3a. Receiver uses its Private Key to decrypt it
Step 3b. Sender uses its Private key to sign and the Receiver's Public key to encrypt it
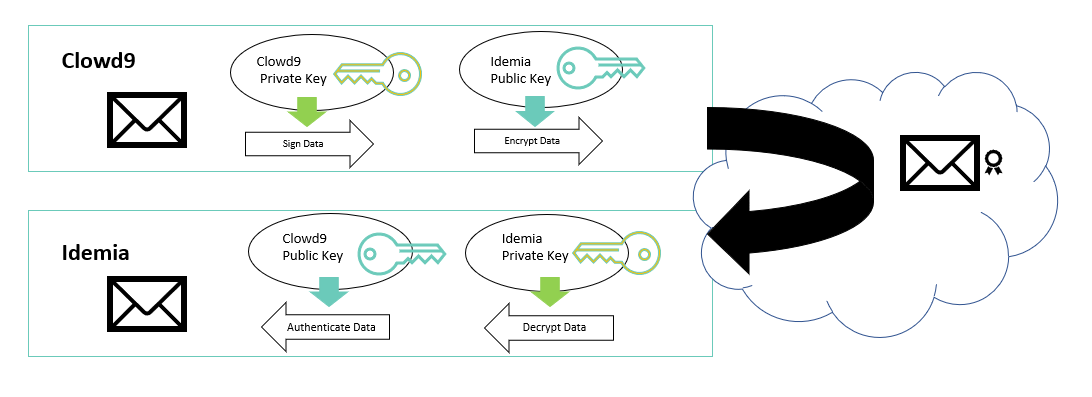
Step 3c. Receiver uses its Private key to decrypt and the Sender’s Public key to validate it
Certificates
To send data securely to a recipient the public key must be used to encrypt it
How to trust that the public key is genuinely the recipient’s one?
Certificates can solve this issue:
A certificate is a Public key signed with the Private key of a trusted authority
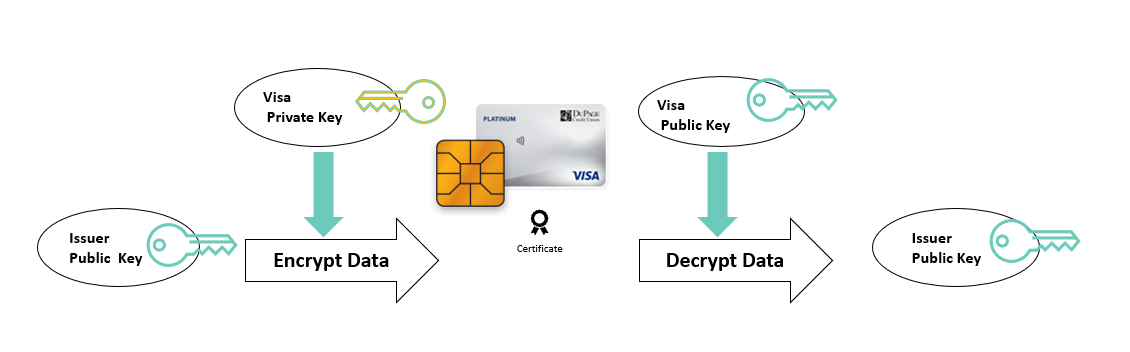
In the above scenario the Issuer certificate in the Chip is verified by the POS terminal using the Visa public key loaded in the terminal. The public key obtained is the trusted Issuer Public key.
Updated 9 months ago