Key Management
What is a key?
A key is a sequence of characters (bytes)
A key can be seen as long a long Password
The length of a key tells how many characters it has: 1 byte = 8 bit so a 2048 bit key is 256 characters long
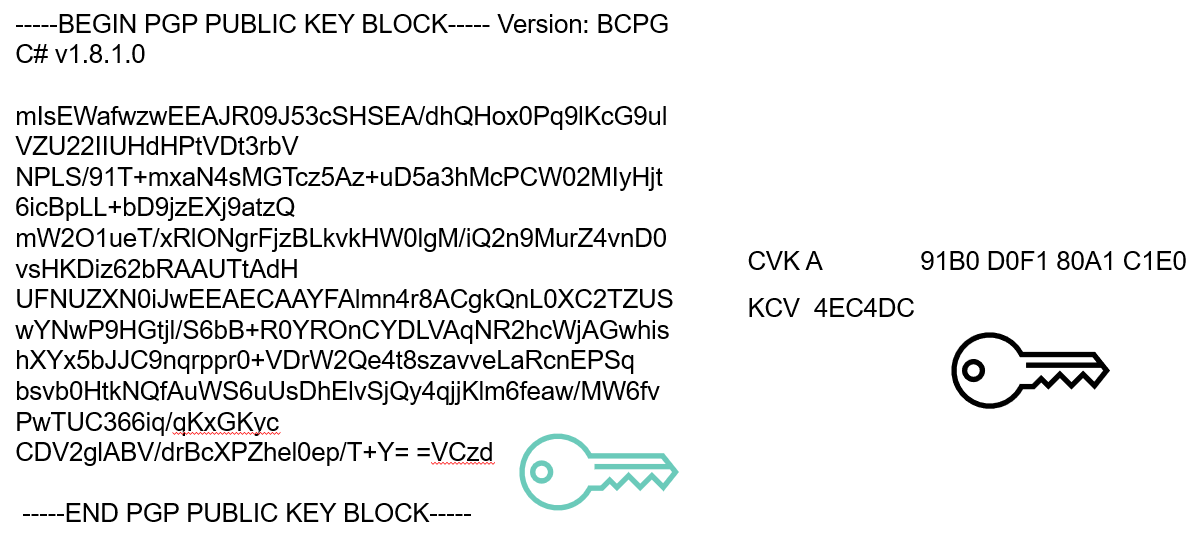
Some keys can contain additional data such as identity of owner (name, domain, email) and expiry date
Note: key can be expressed using hexadecimal value (0-F): 2B 4D 50 6E (4 bytes)
What is it used for?
To encrypt data = make it illegible without the key
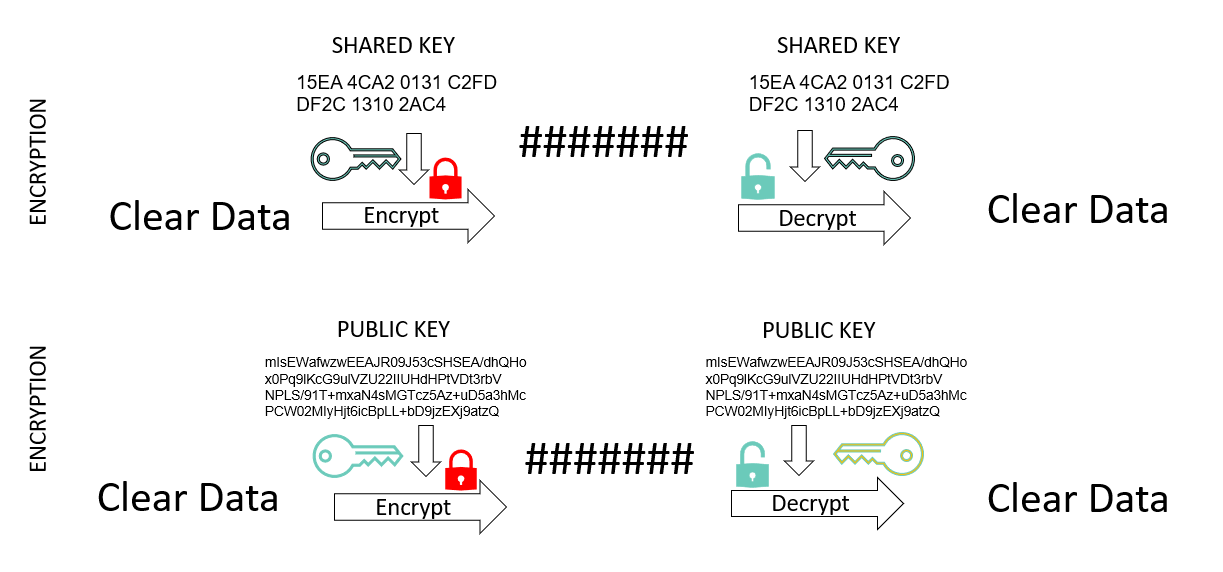
Note: to create a Private Public key pair try PGP Key Generator
To generate verification values
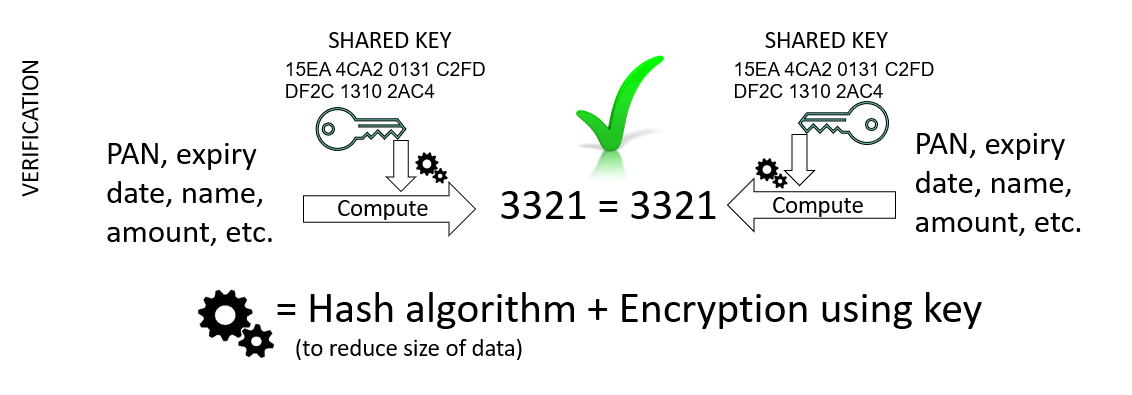
To authenticate data and ensure it has not be altered
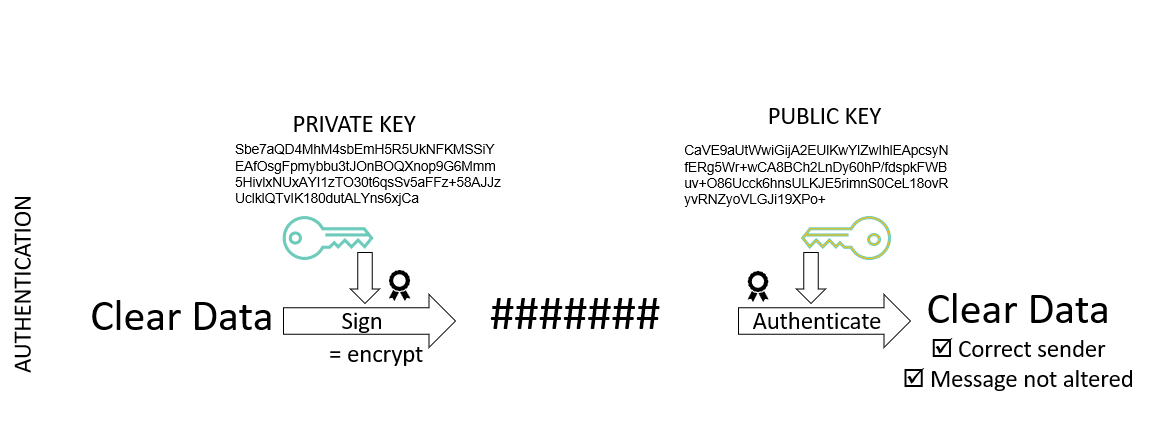
Note: this does not make your message secret . Anybody with our Public Key can decrypt. It only proves that the message can have only been encrypted by you (owner of Private Key).
Different type of keys
Shared key - symmetric
Symmetric keys use the same key for both encryption and decryption.
Both the sender and receiver of the data must share a secret key.
For standard encrypt/decrypt functions, symmetric algorithms generally perform much faster than asymmetrical counterparts.
Symmetric cryptography is efficient for managing large volumes of data.
Private-Public key pair - asymmetric
Asymmetric encryption makes use of a pair of keys a private key and an associated public key
If the public key is used to encrypt data then only the private key can decrypt the data.
Equally, if users with the private key encrypt data then anyone with the public key can decrypt and verify that data.
Asymmetric cryptography is slower and relatively expensive computationally, it works well in situations requiring the benefits of Public Key Infrastructure (PKI). For example when a trusted connection needs to be established where there is not an existing shared symmetric key.
Updated 9 months ago